Autopsy
I consider Autopsy, which comes by default on CAINE and Kali Linux, the first tool to get introduced to forensics due it's graphical and intuitive interface to manage computer forensic tools. Autopsy optimizes the process by using multiple processor cores while running in the background and can tell you in advance if the process will lead to a positive result. Autopsy can also be used as graphical interface for different command line tools, supports extensions for integration with third party tools such as PhotoRec already featured on LinuxHint to improve and add functions.
As said, it comes by default on Kali, Debian and Ubuntu users can get Autopsy by running:
apt install autopsy -y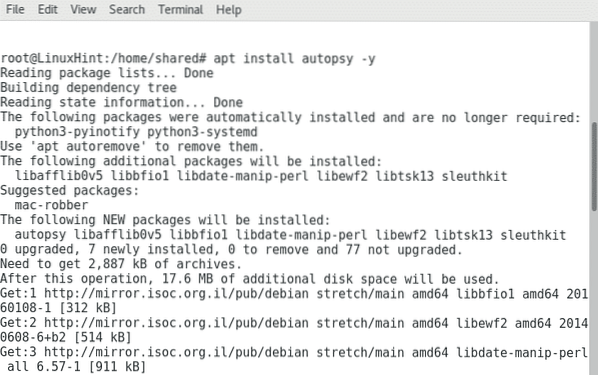
Official website: https://www.sleuthkit.org/autopsy/
CAINE (Computer Aided Investigative Environment)
CAINE is an Ubuntu Linux based distribution specifically designed for computer forensics, it comes with Autopsy by default creating a very friendly environment for the user. CAINE is a great assistant, as an OS, since it applies by default common forensics practices like protecting the storage devices from getting corrupted or overwritten during the forensic process.
CAINE is an up to date Linux distribution highly recommended to get started with computer forensics.
Official website: https://www.caine-live.net/
P0f
P0f is an analyzer for the interaction between different devices through networking. P0f is capable to identify the OS and software used by different devices connected in passive mode, rather than sending packets to analyze the reply P0f only captures packets for later analysis, that's why it can lead to better results than Nmap when fingerprinting. Practical uses of P0f may include detecting an attacker during an ongoing pentesting session, network surveillance and additional information on connections to setup proper security measures. P0f wasn't updated for a long time and has come back as P03 with support for modern OS and software. In a future article we'll trace attackers using different tools including P0f.
Debian and Ubuntu users can install P0f by running:
apt install p0f -y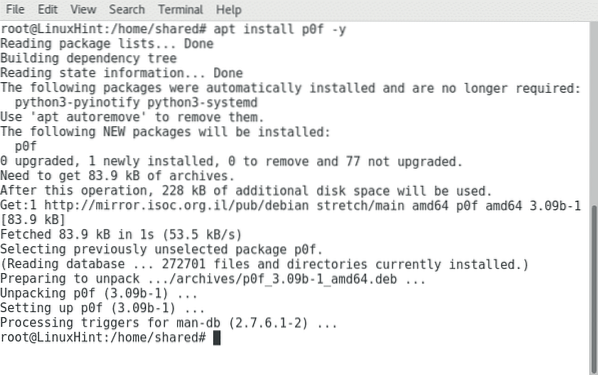
Official website: http://lcamtuf.coredump.cx/p0f3/
Dumpzilla
During a criminal investigation analysis of browsing activity is among the first protocol steps. As said above, Autopsy allows us to enable extensions to research the browsing activity of the user. Dumpzilla is a tool focused specifically on recovering browsing data from Mozilla Firefox browsers or derivatives like Iceweasel or Seamonkey. Dumpzilla can grant us a lot of valuable information like usernames, passwords, browsing history and any information stored in cookies or user preferences. Despite the fact that it is very specific running Dumpzilla against a target with Firefox is recommended, in spite of the fact that it wasn't updated for the last two years.
Dumpzilla isn't included in default repositories, you can get it from: https://github.com/Busindre/dumpzilla
Official website: https://www.dumpzilla.org
Volatility
Volatility allows us to investigate the live RAM of a device, which means information which wasn't stored on the hard drive, but left artifacts or traces on the live RAM. This tool, which comes by default both on CAINE and Kali Linux, can lead us to useful information after an incident on a device, like what processes were running, or are running, during an event. To install volatility on Debian you can run
apt install volatility -y
Official website: https://www.volatilityfoundation.org/
Chkrootkit
A RootKit is malicious software installed locally or remotely on a device to grant illegitimate access to an attacker, we can do a grotesque comparison between rootKits and trojan servers despite small differences (RootKIts include additional functions). RootKits can modify the system files and remove traces of illegitimate intrusions. Here is where ChkRooKit comes analyzing binaries for modifications, logs and other traces which could get removed by an intruder. On Debian you can get chkrootkit by running:
apt install chkrootkit -y
Official website: http://www.chkrootkit.org/
I hope you found this article useful to realize computer forensics are not restricted to IT gurus, anyone can carry out computer forensics easily with the tools mentioned above. Keep following LinuxHint for more tips and updates on Linux.
 Phenquestions
Phenquestions