In networking, a port is an interesting feature. It's a way for network traffic to identify the destination app or service. Each process/service gets its unique port. A port will always be associated with the IP address of the host along with the protocol.
This is a favorite metaphor of mine to describe what a port is. Imagine a ship loaded with cargo, which will travel to a distant land. What information is needed to reach the destination properly? For the sake of simplicity, let's say it needs the country (the IP address) and the port the ship will dock.
In this guide, check out how to list open ports on Linux.
Ports on Linux
Ports act as an endpoint of communication. It's a 16-bit number (0 to 65535 in decimal). While the range is large, for ease of use, ports are categorized into three categories. Each category is labeled as the range of port value:
- 0 to 1023: These are the “Well-known” ports, also known as the “System” ports, which are reserved for system processes that offer a wide variety of network services. To bind with a “Well-known” port, a process must have superuser privilege.
- 1024 to 49151: These are the “Registered” ports, also known as the “User” ports, that are designated by IANA for specific services. Upon request, a process may have access to them. In the case of most systems, it doesn't require any superuser privilege to use these ports.
- 49152 to 65535: These are the “Dynamic” ports, also known as the “Private” ports. These ports can't be registered with IANA. These ports are open to using for private or customized services and may also be automatically allocated as ephemeral ports (short-lived ports used by IP).
In Linux, there are multiple ways of checking the open ports. By default, any port will remain closed unless an app is using it. If a port is open, then it must be assigned to a service/process.
List Open Ports
It's easier to identify which ports are in use rather than which ports are open. That's why the following section will feature methods to list all the ports that are currently in use. In Linux, there are multiple tools available for the task. Most of them come built-in in any Linux distro.
Learning which ports are currently open can be useful in various scenarios. It's possible to configure a dedicated port for a certain application. An open port may also be a strong indication of intrusion in the network.
The following methods are demonstrated on Ubuntu 20.04.1 LTS.
List protocols and open ports from /etc/services
The /etc/services file contains information about the currently running services. It's a big file, so ready to get overwhelmed.
$ cat /etc/services | less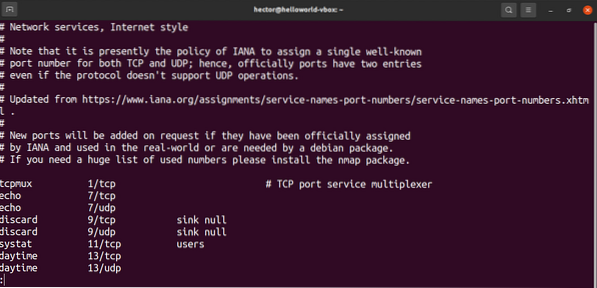
List open ports using netstat
The netstat tool is a utility for displaying network connections for TCP, routing tables, and various network interfaces. It also offers network protocol statistics. By using netstat, we can list all the open ports of the system.
Run the following netstat command:
$ netstat -atu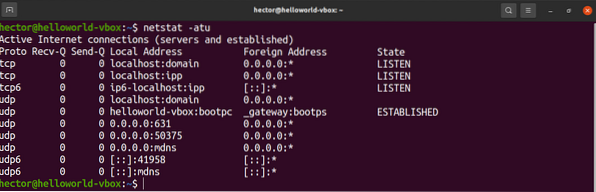
Let's have a quick breakdown of all the flags we used in this command.
- a: Tells netstat to show all sockets
- t: Tells netstat to list TCP ports
- u: Tells netstat to list UDP ports
Here's another variation of the netstat command:
$ netstat -lntu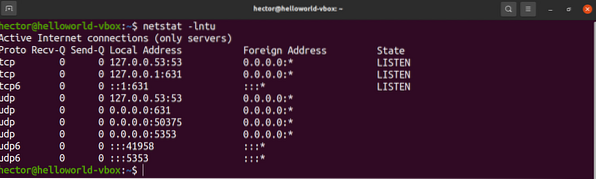
There are two new flags used in the command. What do they mean?
- l: Tells netstat to print only the listening sockets
- n: Tells netstat to show the port number
To display the PID of the process that's using a port, use the “-p” flag:
$ netstat -lntup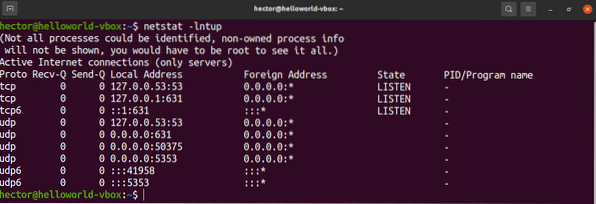
List open ports using ss
The ss tool is a utility for investigating socket. Its usage is similar to netstat.
To list the open ports, run the following ss command:
$ ss -lntu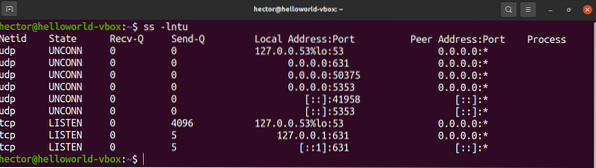
The flags are similar to netstat. The functions they describe are also quite similar.
- l: Tells ss to display listening sockets
- n: Tells ss not to try to resolve service names
- t: Tells ss to display TCP sockets
- u: Tells ss to display UDP sockets
List open ports using lsof
The lsof command is to list open files. However, it can also be used for displaying the open ports.
Run the following lsof command:
$ lsof -i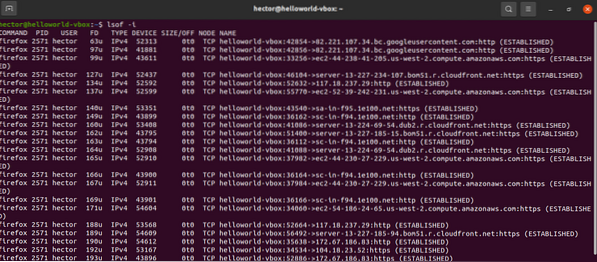
To get the open ports of a specific protocol (TCP, UDP, etc.) then define it after the “-i” flag, use:
$ lsof -i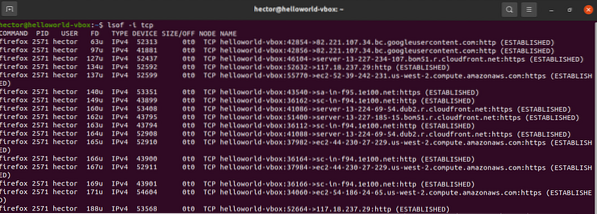
List open ports using nmap
The nmap tool is a powerful one for network exploration and security/port scanning. It can report all the open ports in the system.
To list the open TCP ports, run the following nmap command. Here, the IP address is of the host computer:
$ sudo nmap -sT -p- localhost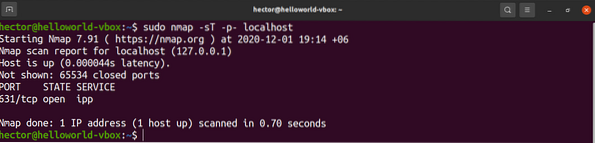
Here, there are two portions of the command argument.
- -sT: This section tells nmap to scan for TCP ports.
- -p- : This tells nmap to scan for all 65535 ports. If not used, then nmap will scan only 1000 ports by default.
If you need to list the open UDP ports, then run the following nmap command:
$ sudo nmap -sU -p- localhost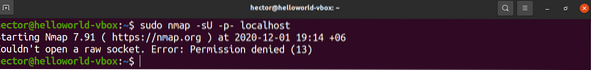
To get both the open TCP and UDP ports, use the following command:
$ sudo nmap -n -PN -sT -sU -p- localhostList open ports using netcat
The netcat tool is a command line utility for reading and writing data across network connections over the TCP and UDP protocols. This tool can also be used for listing open ports. It can perform tests on a specific port or a range of ports.
The following netcat command will scan the port from 1 to 1000. The netcat command will perform the scan on TCP protocol by default:
$ nc -z -v localhost 1-1000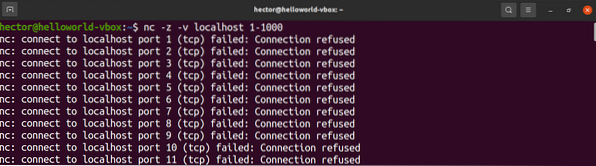
It can also be extended to the entire list of possible ports:
$ nc -z -v localhost 1-65535
Let's have a quick breakdown of the flags.
- z: Tells netcat to scan only for open ports without sending any data
- v: Tells netcat to run in verbose mode
To get only the open ports from this list, filter the output with grep for the term “succeeded”.
$ nc -z -v localhost 0-65535 2>&1 | grep succeededIf you want to perform the scan on UDP protocol, then add the “-u” flag.
$ nc -z -v -u localhost 0-65535 2>&1 | grep succeededFinal Thoughts
As demonstrated, there are tons of ways to scan for open ports on Linux. I suggest trying out all the methods before you decide which one to master. If you're using a certain tool like netcat or nmap regularly, then mastering the associated methods will be the most beneficial.
Happy computing!
 Phenquestions
Phenquestions